Disabling root SSH access with a password while allowing login via SSH keys is a highly recommended security practice. This ensures that only users with the correct SSH key can access the root account, eliminating the risk of brute-force attacks on root passwords.
Prerequisites #
- SSH Access to the Server:
- You must have SSH access to the server as either the root user or a sudo user.
- Root SSH Key:
- You should already have an SSH key configured for the root user, or you need to set one up before disabling password access.
- If you don’t have an SSH key yet, follow these instructions to generate and copy an SSH key to the server before proceeding.
- Sudo User with SSH Access (Optional but recommended):
- It’s always good practice to have a non-root sudo user with SSH access for emergency purposes.
Step-by-Step Guide to Disable Root SSH with Password but Enable SSH Keys #
Follow the steps below to
Step 1: Verify or Set Up SSH Keys for Root #
- If you haven’t generated SSH key on your local machine and uploaded it on the server, follow these steps to generate and uplaod the key.
Step 2: Backup the SSH Configuration File #
- Access the server via SSH as guided here.
- Before making any changes on the server, back up the current SSH configuration on the server. This ensures you can restore the original settings if something goes wrong.
cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bakStep 3: Edit the SSH Configuration File #
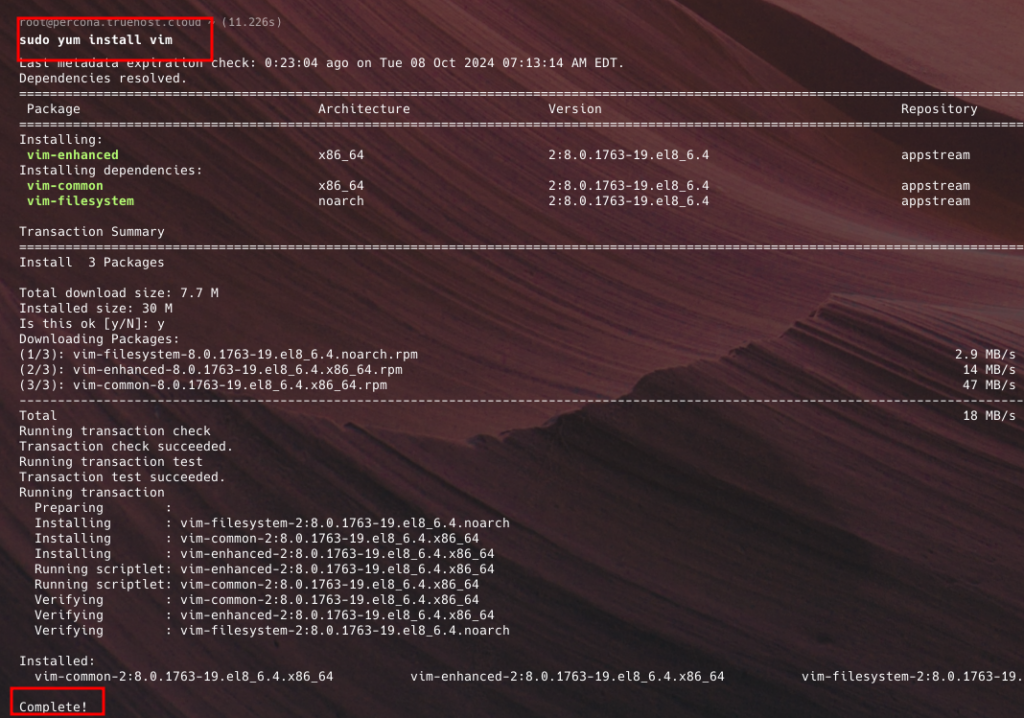
- If you have not installed vim or nano, you may want to install them first using either sudo apt-get install vim / sudo apt-get install nano (ubuntu, dedian, mint) or sudo yum install vim /sudo yum install nano (centos, almalinux, redhat)
- Open the SSH configuration file for editing, using your favorite text editor like nano or vim.
vim /etc/ssh/sshd_confignano /etc/ssh/sshd_config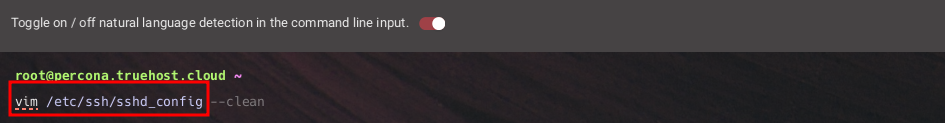
Look for the following lines (you may need to uncomment some of them):
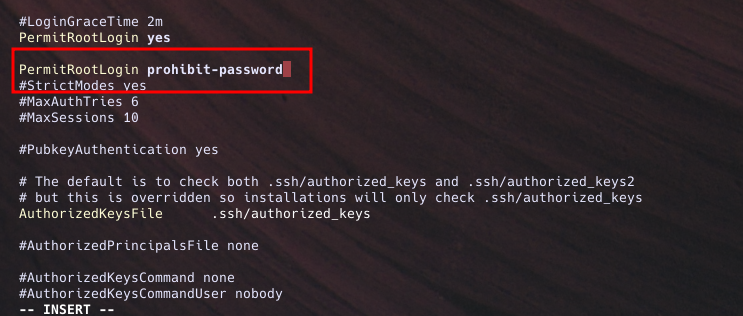
A. Disable root login with a password: Find the line that specifies PermitRootLogin & modify it as follows:
PermitRootLogin prohibit-password- This setting allows root login only via SSH keys and disables password-based root logins.
B. Disable password authentication (for all users): For extra security, you may want to disable password authentication entirely and enforce SSH key authentication for all users. Do that by adding this setting below. Well, unless if you really want to, I would suggest you do not disable passwords for all users. S
PasswordAuthentication no
Step 4: Reload the SSH Service #
To apply the changes, reload the SSH service:
systemctl reload sshd OR systemctl reload sshd.serviceStep 5: Test SSH Key Login for Root
- Do not log out of your current session yet.
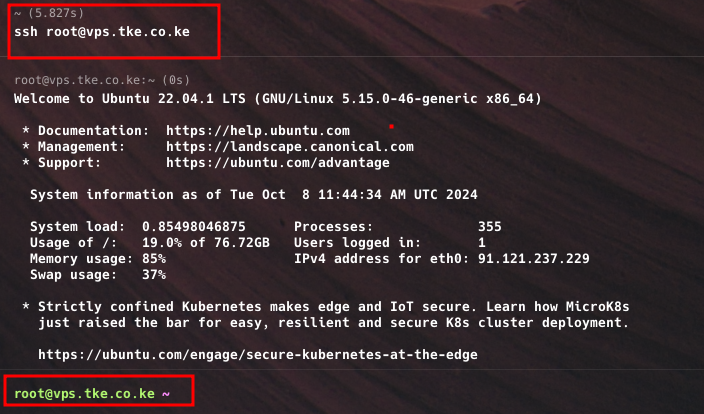
- Open a new terminal window and test the SSH key-based login for root:
ssh root@your_server_ip- If the login succeeds, your SSH keys are working correctly. You can now close your original session.
- If you want to disable password authentication for all users other than root (I discourage), proceed to step 6 below,
Step 6: Ensure Non-Root Users Can Still Log In (Optional)
- If you are enforcing SSH keys for all users, make sure that any non-root users also have their SSH keys set up. Otherwise, they will be locked out once password authentication is disabled.
- To add SSH keys for a non-root user, follow the same steps as for root: log in as the non-root user and place the public key in
~/.ssh/authorized_keysfor that user. - Alternatively use the command below; replace username with the actual user
ssh-copy-id useraneme@your_server_ipStep 7: Restart SSH Service (If Required) #
After making final adjustments, you can restart the SSH service to ensure everything is properly configured:
systemctl restart sshd OR systemctl restart sshd.service