System logs in Linux are essential for monitoring, troubleshooting, and maintaining a secure, well-functioning environment.
Logs contain records of all activities on the system, ranging from user actions to system errors, application events, and kernel messages.
Managing logs effectively helps you gain insight into system performance, security incidents, and application behavior, enabling better decision-making for maintaining and securing your Linux environment.
1. What Are System Logs? #
System logs record events that happen on a Linux system, capturing details of operations performed, user actions, errors, warnings, and application-specific events
These logs are critical for diagnosing issues, auditing user actions, and ensuring security compliance.
Logs are often organized by category, with standard directories where log files are stored.
Common Log Types:
- System Logs: General system activities (e.g.,
syslog,kern.log) - Authentication Logs: User login activities and authentication errors (e.g.,
auth.log) - Application Logs: Application-specific events (e.g., web server logs)
- Kernel Logs: Events related to the kernel and hardware (
dmesglogs) - Boot Logs: System boot-related logs (
boot.log)
2. Locating System Logs #
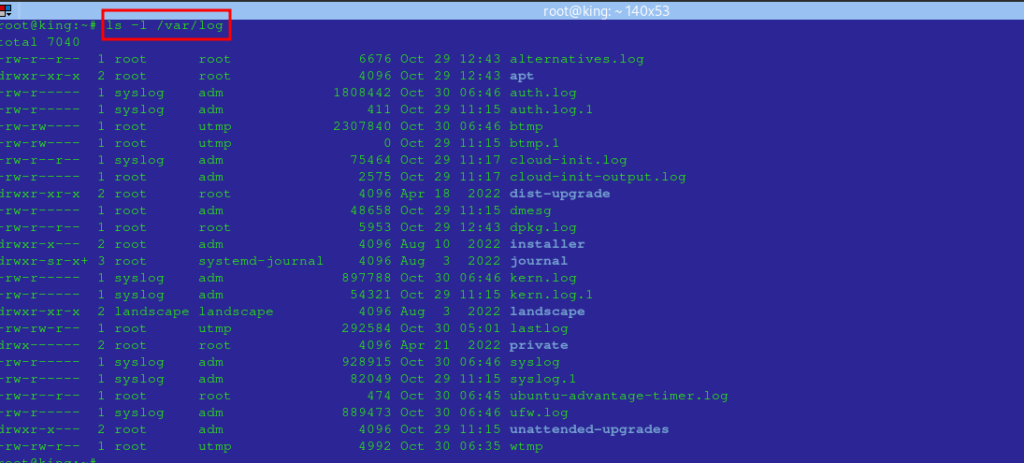
On most Linux distributions, log files are stored in the /var/log directory, where they are categorized by the type of log. Below are a few examples of common logs in this directory:
| Log File | Description |
|---|---|
/var/log/syslog | System and application messages |
/var/log/auth.log | User login and authentication details |
/var/log/kern.log | Kernel messages and events |
/var/log/dmesg | Boot and hardware-related messages |
/var/log/messages | General messages (on some distros) |
/var/log/boot.log | Boot-related events |
Tip: Use the ls -l /var/log command to explore available logs in this directory
3. Viewing Logs #
To view logs, you can use commands such as cat, tail, less, and grep to filter and display log information. Below are a few common ways to access and view logs in real-time.
tailCommand: To monitor the latest entries in a log file in real-time:
tail -f /var/log/syslog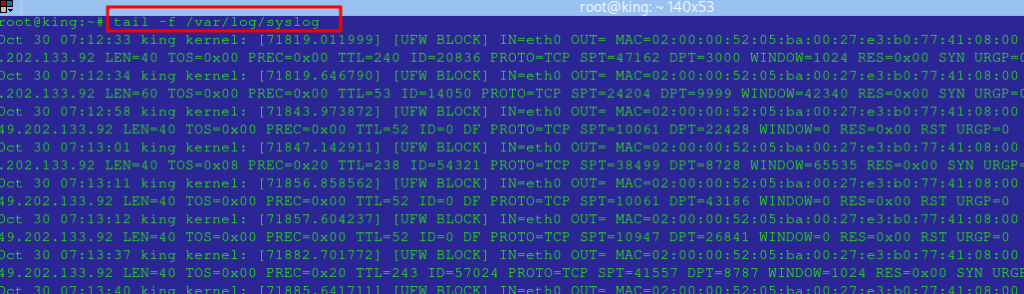
catCommand: To view the entire content of a log file:- This command can return a lot of data since you are viewing everything in a file
cat /var/log/auth.loglessCommand: For easier navigation through large logs:
less /var/log/kern.loggrepCommand: To search for specific keywords in logs:
grep "error" /var/log/syslog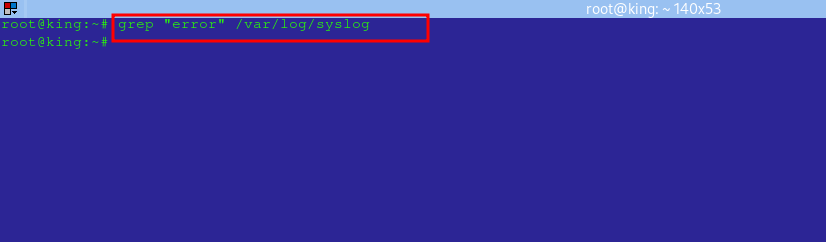
- In the image above, the command returns no result since the file /var/log/syslog has no line that has the name “error.”
4. Understanding Log Rotation #
Log rotation is essential for managing log file sizes to prevent storage issues. On Linux, logrotate is a built-in utility that rotates, compresses, and removes old log files to ensure only recent logs are active.
- Configuration: Log rotation is configured in
/etc/logrotate.confand specific application files in/etc/logrotate.d/. - Customizing Rotation: You can set the frequency, number of archived files to keep, and compression settings in configuration files.
To test logrotate, the command below. Note that running the command will;
- Log files defined in
/etc/logrotate.confor referenced within this file (e.g., from/etc/logrotate.d/) will be rotated even if they would not usually be rotated at this time. - If the configuration specifies,
logrotatewill create new log files to replace the rotated ones, such as movinglogfile.logtologfile.log.1and creating a newlogfile.log. - Will perform any other actions as defined in the /etc/logrorate.conf
sudo logrotate -f /etc/logrotate.conf5. Managing and Archiving Logs #
Archiving old logs can free up space and keep logs organized. You can use tools like gzip to compress log files:
gzip /var/log/syslog.1To automate log archival, add custom configurations in logrotate to compress logs automatically after a certain number of rotations.
6. Monitoring Logs with journalctl #
Most modern Linux distributions use systemd and journalctl for centralized log management. This enables more efficient log filtering and viewing.
Basic Usage: To view the entire journal:
journalctl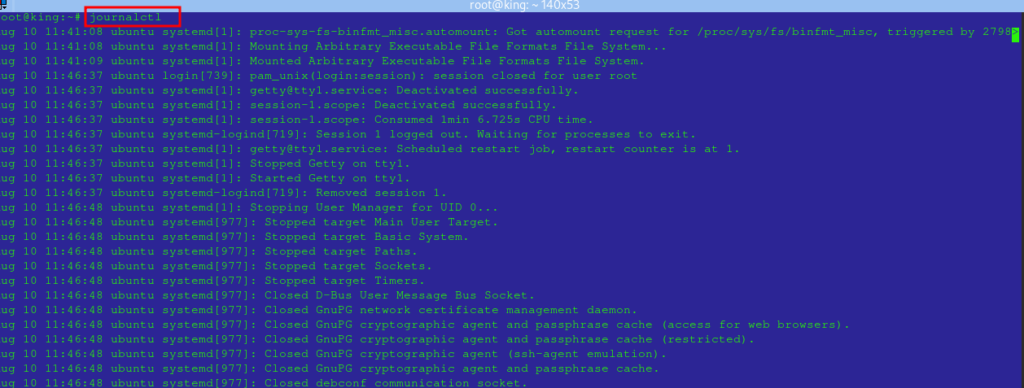
Filtering by Time: To view logs within a specific timeframe:
journalctl --since "2023-01-01" --until "2023-01-02"
Filtering by Service: To view logs for a specific service (e.g., ssh):
journalctl -u ssh
Royal tip: Note that journalctl -f shows: real-time logs, similar to tail -f.
7. Implementing Log Analysis Tools #
For advanced log management, analysis tools such as ELK Stack (Elasticsearch, Logstash, Kibana) and Graylog can aggregate logs from multiple sources, offer real-time insights, and alert on abnormal patterns.
8. Best Practices for Log Management #
- Enable Centralized Logging: Centralize logs to simplify monitoring and avoid data loss.
- Set Up Log Rotation: Configure
logrotateto avoid excessive disk usage. - Limit Log Retention: Retain logs only as long as necessary for compliance and monitoring.
- Implement Access Control: Restrict log file access to authorized users.
- Monitor Logs for Security Incidents: Regularly review logs for unauthorized access and errors.
Final word #
Understanding and managing system logs in Linux is critical for server maintenance, troubleshooting, and security. By effectively utilizing tools like journalctl, logrotate, and third-party solutions, you can streamline log management and gain better insights into your system’s behavior.