Configuring SSH keys for a user on your server is a secure way to authenticate without using a password. Below is a step-by-step guide on how to configure SSH key-based authentication for a user.s
If you haven’t set up SSH key authentication for the root user, follow these steps to generate and add the key.
Prerequisites #
- Access to the server:
You must have access to the server as a root or sudo user. See this. - User account:
Ensure the user account already exists on the server or create a new user if needed. - SSH client:
The local machine must have an SSH client installed (usually built-in for Linux/macOS or using tools like PuTTY for Windows).
Step-by-Step Guide to Configure SSH Key for a User #
Follow these steps below to generate SSH key on your computer and uplaod to a server for secure access.
Step 1: Generate an SSH Key Pair (On Local Machine) #
- On your local computer, generate an SSH key pair (public and private key). This is done on your local system where you will connect from:
ssh-keygen -t rsa -b 4096- You will be prompted to enter a file name to save the key (press Enter to accept the default path
~/.ssh/id_rsa). - Optionally, enter a passphrase to add an extra layer of security. Consider not to do that.
- That command above will create two files;
~/.ssh/id_rsa(private key, do not share this)~/.ssh/id_rsa.pub(public key)
Step 2: Copy the Public Key to the Server #
- Once you have the SSH key pair, you need to copy the public key to the server for the specific user. Use the following command to transfer the public key to the server:
- Replace
usernamewith the user’s name (e.g root or another user) andserver_ipwith your server’s IP address.
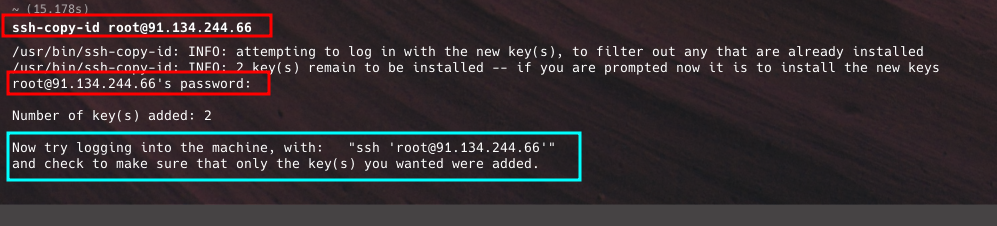
ssh-copy-id username@server_ip- If you are using a custom SSH port, other than 22, you will need to cater for that in your command using the -p port_number as shown below;
ssh-copy-id -p 2258 username@server_ip- You will be asked to input password for the user. Do that to complete the key-set up process.
Alternatively, you can manually copy the public key using the following method if ssh-copy-id is not available:
- On your local machine, display the public key using this command, then copy the output of the public key, for you will pate need it in one the next steps.
cat ~/.ssh/id_rsa.pub- On the server, log in via SSH and switch to the user account, if you are not configuring for root:
ssh root@server_ip
su - username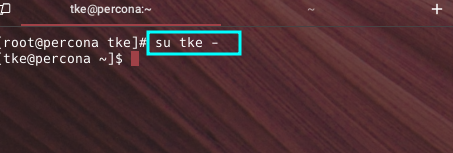
- On the server, create the
.sshdirectory and theauthorized_keysfile for the user (if it doesn’t exist) - Use these commands below;
mkdir -p ~/.ssh
touch ~/.ssh/authorized_keys
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keys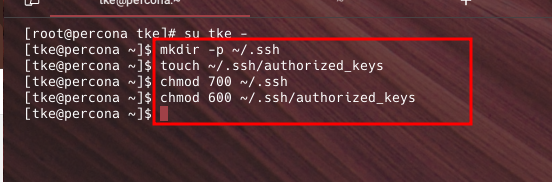
- Paste the public key (you had copied it ealier) into the
authorized_keysfile either copying and pasting into the file or using the command below;
echo "your-public-key-content" >> ~/.ssh/authorized_keys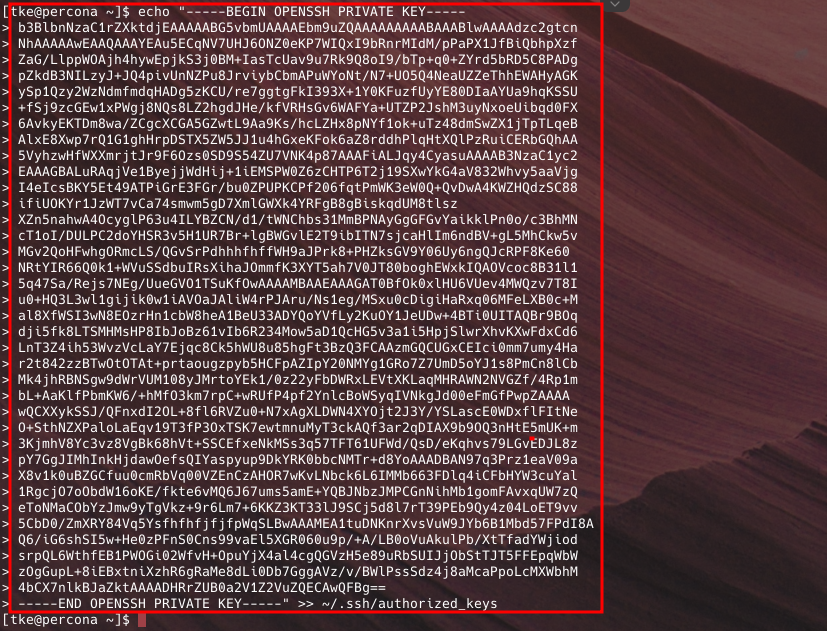
Step 3: Test SSH Key Login #
- On your local machine, test logging in to the server using the SSH key:
ssh username@server_ip- If you has entered a passphrase while generating the key, you’ll be prompted to enter it. If the setup was done correctly, you should be logged in without needing a password for the user account.