Disabling root access via SSH is a common security measure to prevent unauthorized access to your server. Instead of logging in as root, users should log in as a regular user and elevate their privileges using sudo.
Prerequisites #
Before disabling root SSH access, ensure the following:
- You must have SSH access to the server, either as the root user or a sudo user.
- Ensure that you have a non-root user with sudo privileges set up on the server. Use these steps to create one
Step 1: Log in to Your Server. Check these steps on how to do that. #
Step 2: Create or Verify a Sudo User #
- If you do not already have a sudo user, create one before disabling root SSH access.
- If you have a user already, very that the user can run sudo commands by running the command below.
- If the command returns
root, the new user has sudo privileges. You may then proceed, otherwise refer to this article.
sudo whoamiStep 3: Backup the SSH Configuration File #
- Before making any changes, create a backup of the SSH configuration file:
- This allows you to restore the configuration if necessary. Use the command below.
cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak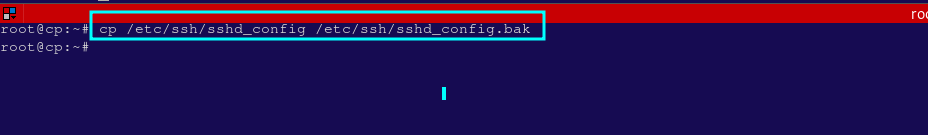
Step 4: Edit the SSH Configuration File #
- Open the SSH configuration file using a text editor, such as vim or nano:
vim /etc/ssh/sshd_config or nano /etc/ssh/sshd_config
- Locate the line that allows root login:
PermitRootLogin yes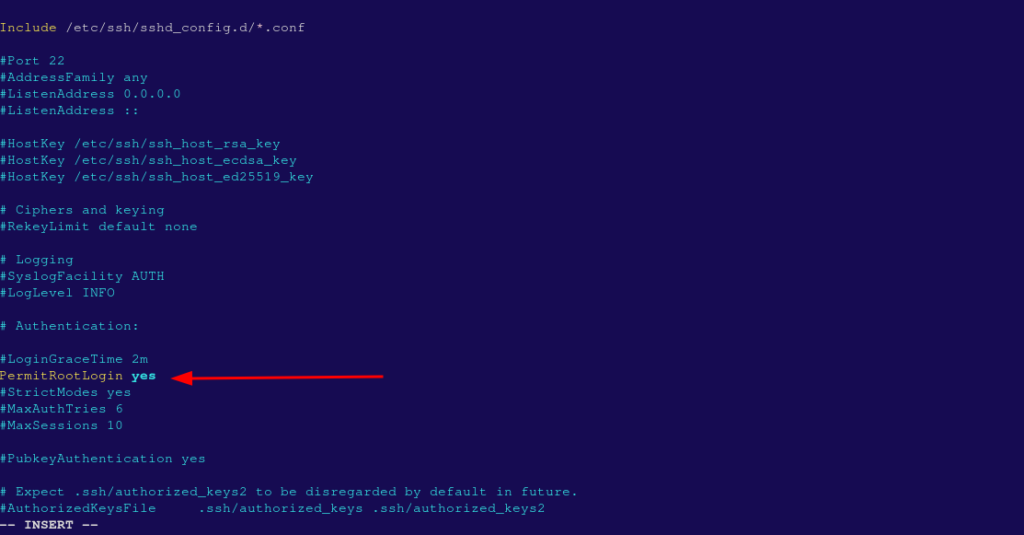
- Change it to:
PermitRootLogin noThis disables SSH access for the root user.
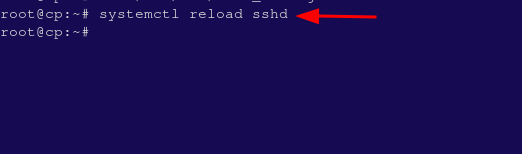
Step 5: Reload SSH Service #
- After editing the SSH configuration file, reload the SSH service to apply the changes:
systemctl reload sshd OR systemctl reload sshd.service