A firewall is a fundamental tool for securing your server, as it controls incoming and outgoing network traffic based on predetermined rules. For Linux servers, UFW (Uncomplicated Firewall) is a popular choice due to its simplicity and ease of use, even for those new to Linux system administration
Originally developed for Ubuntu, UFW has since been adopted by other Debian-based systems and even some non-Debian-based distributions, thanks to its efficiency and straightforward command structure.
Supported Operating Systems #
- Ubuntu (all LTS and newer versions)
- Debian (and many of its derivatives)
- Linux Mint
- Kali Linux
- Raspberry Pi OS (Raspbian)
On Red Hat-based systems like CentOS, RHEL, and Fedora, UFW can be installed but is less common, as these distributions typically use firewalld as their primary firewall tool.
How to Set Up UFW on Your Linux Server #
In this article, we will use a server that has Ubuntu 22.04 installed
Step 1: Update your server #
- First, start by updating apckages on your server. Use the command below to do that.
sudo apt update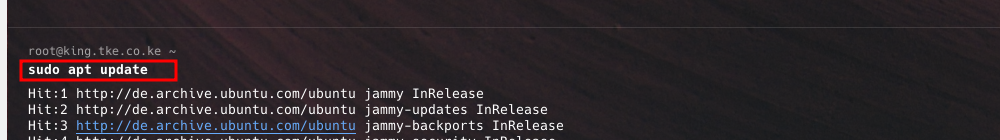
Step 2: Install UFW #
- Run the command below to install
- This command will install UFW and any required dependencies.
sudo apt install ufw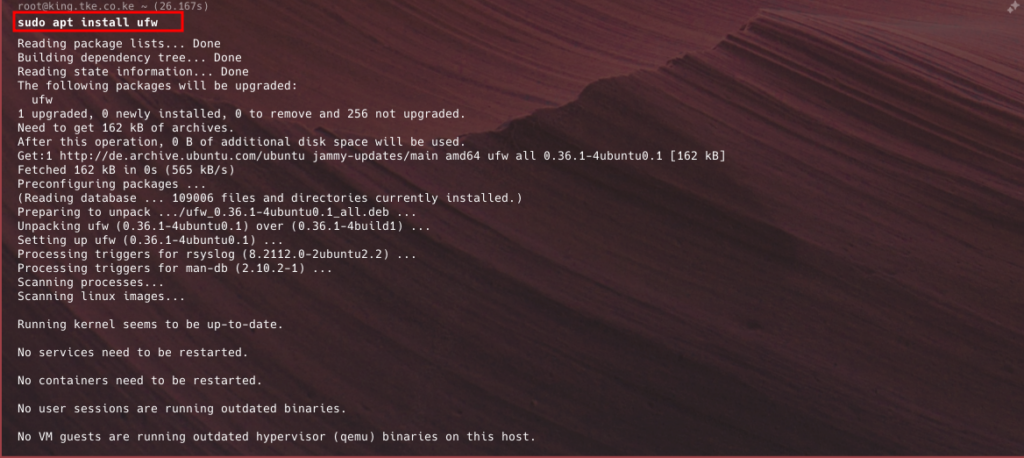
Step 2: Set Up Default Rules #
- These rules help determine the overall security level of your firewall.
- It’s generally best practice to deny all incoming connections and allow all outgoing connections by default. This ensures that only the traffic you explicitly allow can access your server.
Deny Incoming Connections:
sudo ufw default deny incomingAllow Outgoing Connections:
sudo ufw default allow outgoing
- These default policies establish a secure baseline by only allowing connections to services you specify.
Step 3: Allow Specific Ports and Services #
- After setting up default rules, you’ll need to allow connections to essential services.
Allow SSH (Port 22) – SSH allows remote access to your server, so allowing this port is critical if you want to maintain access.
sudo ufw allow ssh
Alternatively, if SSH is running on a different port, replace ssh with the port number, for example:
sudo ufw allow 2222
Allow HTTP and HTTPS – If your server hosts a website, you’ll need to allow HTTP (port 80) and HTTPS (port 443) traffic.
sudo ufw allow http
sudo ufw allow https
Allow Other Services – You can specify any additional services by their port number or name. For example, to allow MySQL (port 3306) or other specific ports:
sudo ufw allow 3306Step 4: Enable UFW #
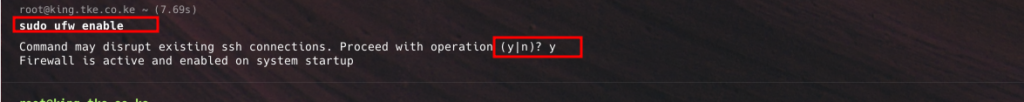
Once you’ve defined your rules, enable UFW to activate the firewall. UFW will immediately apply the rules.
sudo ufw enableYou’ll be prompted to confirm your choice. Enabling UFW will enforce the rules you’ve configured to secure your server.
Step 5: Verify UFW Status and Rules
- After enabling UFW, check its status to ensure your rules are correctly applied:
- This command provides a list of active rules, showing which ports and services are allowed or denied.
sudo ufw status verbose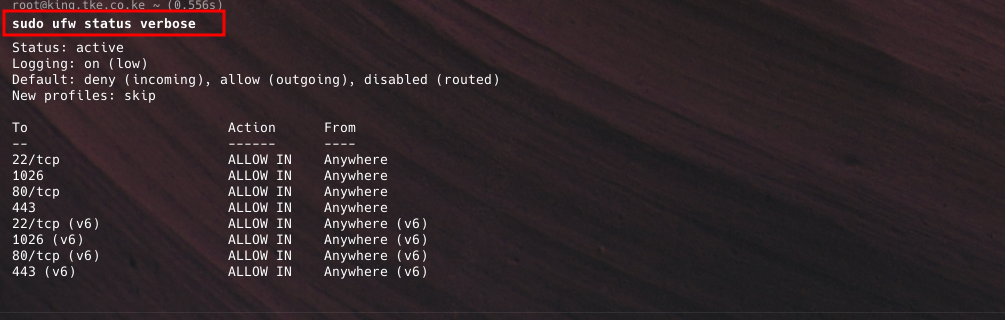
Step 6: Configure IP-Based Restrictions (Optional) #
- UFW can allow or deny traffic based on specific IP addresses. This is useful for restricting access to certain services or adding extra security.
Allow Connections from a Specific IP:
sudo ufw allow from 192.168.1.100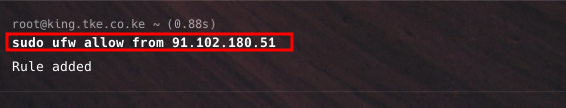
Deny Connections from a Specific IP:
sudo ufw deny from 192.168.1.100
Allow an IP Address on a Specific Port:
sudo ufw allow from 192.168.1.100 to any port 22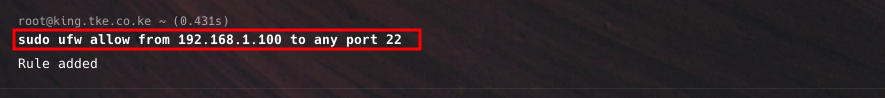
These rules provide more granular control, which can help limit access to critical services.
Step 7: Disable UFW (if necessary)
To turn off UFW, use the following command:
sudo ufw disable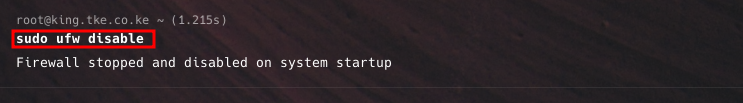
This command disables the firewall, though you can re-enable it at any time using
sudo ufw enableStep 8: Remove or Modify Existing Rules #
To delete or modify an existing rule, first list rules by numbering them:
sudo ufw status numbered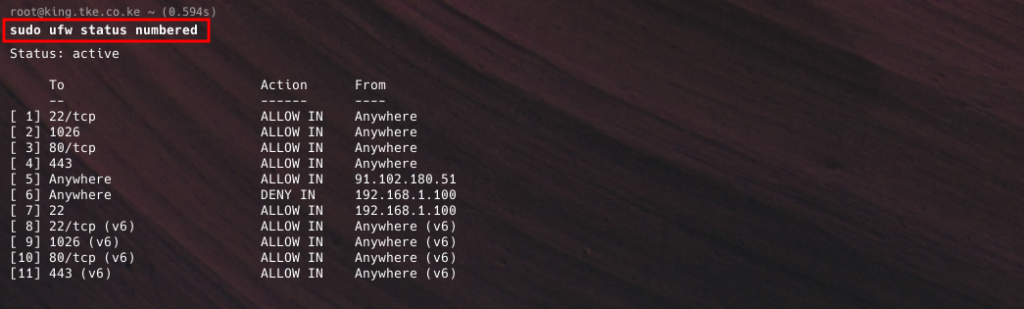
To delete a specific rule, use its rule number:
sudo ufw delete <rule-number>In the image below, we delete rule number 6 using sudo ufw delete 6

This is useful when you need to make adjustments to your firewall configuration.
Setting up a firewall is essential for securing a server, and UFW makes it easy to implement a basic firewall configuration on Linux. By following the steps outlined here, you can limit access to essential services, control connections from specific IPs, and maintain a secure server environment with minimal configuration.